| 知乎專欄 | 多維度架構 | 微信號 netkiller-ebook | QQ群:128659835 請註明“讀者” |
http://www.strongswan.org/
User -> Windows 10 Desktop -> Inside Greatwall -> VPN Server(Hongkong/Other) -> Outside Greatwall
首先在海外部署一台伺服器,將伺服器配置成為VPN伺服器,然後桌面用戶通過該伺服器,你懂的......
由於pptp,l2tp,openvpn 先後被牆,所以我選擇了IKEv2。
CentOS 7 環境
yum install -y strongswane yum install -y haveged systemctl enable haveged systemctl start haveged cd /etc/strongswan
創建自簽名CA根證書
# 私鑰證書 strongswan pki --gen --type rsa --size 4096 --outform der > ipsec.d/private/CARootKey.der chmod 600 ipsec.d/private/CARootKey.der # 公鑰證書 strongswan pki --self --ca --lifetime 3650 --in ipsec.d/private/CARootKey.der --type rsa --dn "C=NL, O=Example Company, CN=StrongSwan Root CA" --outform der > ipsec.d/cacerts/CARootCert.der strongswan pki --print --in ipsec.d/cacerts/CARootCert.der
頒發伺服器證書
# 私鑰證書 strongswan pki --gen --type rsa --size 2048 --outform der > ipsec.d/private/ServerKey.der chmod 600 ipsec.d/private/ServerKey.der # 公鑰證書 strongswan pki --pub --in ipsec.d/private/ServerKey.der --type rsa | strongswan pki --issue --lifetime 730 --cacert ipsec.d/cacerts/CARootCert.der --cakey ipsec.d/private/CARootKey.der --dn "C=NL, O=Example Company, CN=vpn.example.org" --san vpn.example.com --san vpn.example.net --san 147.90.44.87 --san @147.90.44.87 --flag serverAuth --flag ikeIntermediate --outform der > ipsec.d/certs/ServerCert.der strongswan pki --print --in ipsec.d/certs/ServerCert.der
頒發客戶端用戶證書
# 私鑰證書 cd /etc/strongswan/ strongswan pki --gen --type rsa --size 2048 --outform der > ipsec.d/private/ClientKey.der chmod 600 ipsec.d/private/ClientKey.der # 公鑰證書 strongswan pki --pub --in ipsec.d/private/ClientKey.der --type rsa | strongswan pki --issue --lifetime 730 --cacert ipsec.d/cacerts/CARootCert.der --cakey ipsec.d/private/CARootKey.der --dn "C=NL, O=Example Company, CN=netkiller@msn.com" --san "netkiller@msn.com" --san "neo.chan@live.com" --outform der > ipsec.d/certs/ClientCert.der # 證書轉換,轉過過程是 der -> pem -> p12 openssl rsa -inform DER -in ipsec.d/private/ClientKey.der -out ipsec.d/private/ClientKey.pem -outform PEM openssl x509 -inform DER -in ipsec.d/certs/ClientCert.der -out ipsec.d/certs/ClientCert.pem -outform PEM openssl x509 -inform DER -in ipsec.d/cacerts/CARootCert.der -out ipsec.d/cacerts/CARootCert.pem -outform PEM # 請為證書設置一個密碼 openssl pkcs12 -export -inkey ipsec.d/private/ClientKey.pem -in ipsec.d/certs/ClientCert.pem -name "Client's VPN Certificate" -certfile ipsec.d/cacerts/CARootCert.pem -caname "strongSwan Root CA" -out Client.p12
p12中包含了CA證書,客戶端私鑰證書,客戶端公鑰證書。Client.p12 發送給最終用戶即可
![[提示]](../../../graphics/tip.png) | 提示 |
|---|---|
|
如果你安裝過 OpenVPN 那麼會很好理解,上述的幾個步驟等同於: build-ca = CARootKey/CARootCert build-key-server server = ServerKey/ServerCert build-key client1 = Client.p12 |
開啟轉發
cat > /etc/sysctl.d/vpn.conf <<EOF # VPN net.ipv4.ip_forward = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 EOF sysctl -p /etc/sysctl.d/vpn.conf
開放500,4500兩個連接埠,注意是UDP協議,允許esp,ah協議通過,最後IP偽裝
# for ISAKMP (handling of security associations) iptables -A INPUT -p udp --dport 500 --j ACCEPT # for NAT-T (handling of IPsec between natted devices) iptables -A INPUT -p udp --dport 4500 --j ACCEPT # for ESP payload (the encrypted data packets) iptables -A INPUT -p esp -j ACCEPT iptables -A INPUT -p ah -j ACCEPT # for the routing of packets on the server iptables -I POSTROUTING -t nat -o eth1 -j MASQUERADE iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to-source xxx.xxx.xxx.xxx
xxx.xxx.xxx.xxx 改為你的出口IP,也就是 eth1的IP地址。
啟動 strongswan 服務
如果你使用 CentOS 7 firewalld 請用下面命令
firewall-cmd --zone=dmz --permanent --add-rich-rule='rule protocol value="esp" accept' # ESP (the encrypted data packets) firewall-cmd --zone=dmz --permanent --add-rich-rule='rule protocol value="ah" accept' # AH (authenticated headers) firewall-cmd --zone=dmz --permanent --add-port=500/udp #IKE (security associations) firewall-cmd --zone=dmz --permanent --add-port=4500/udp # IKE NAT Traversal (IPsec between natted devices) firewall-cmd --permanent --add-service="ipsec" firewall-cmd --zone=dmz --permanent --add-masquerade firewall-cmd --permanent --set-default-zone=dmz firewall-cmd --reload firewall-cmd --list-all
下面配置 IPSEC 複製粘貼即可
cp /etc/strongswan/ipsec.conf{,.original}
cat > /etc/strongswan/ipsec.conf <<EOF
# ipsec.conf - strongSwan IPsec configuration file
config setup
charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2"
conn %default
keyexchange=ikev2
ike=aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes256-sha256-modp2048,aes256-sha1-modp2048,aes128-sha256-modp1024,aes128-sha1-modp1024,aes256-sha384-modp1536,aes256-sha256-modp1536,aes256-sha1-modp1536,aes256-sha384-modp1024,aes256-sha256-modp1024,aes256-sha1-modp1024!
esp=aes128gcm16-ecp256,aes256gcm16-ecp384,aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes256-sha256-modp2048,aes256-sha1-modp2048,aes128-sha256-modp1024,aes128-sha1-modp1024,aes256-sha384-modp1536,aes256-sha256-modp1536,aes256-sha1-modp1536,aes256-sha384-modp1024,aes256-sha256-modp1024,aes256-sha1-modp1024,aes128gcm16,aes256gcm16,aes128-sha256,aes128-sha1,aes256-sha384,aes256-sha256,aes256-sha1!
dpdaction=clear
dpddelay=300s
rekey=no
left=%any
leftsubnet=0.0.0.0/0
leftcert=ServerCert.der
right=%any
rightdns=8.8.8.8,8.8.4.4
rightsourceip=10.10.0.0/24
conn IPSec-IKEv2
keyexchange=ikev2
auto=add
conn IPSec-IKEv2-EAP
also="IPSec-IKEv2"
rightauth=eap-mschapv2
rightauthby2=pubkey
rightsendcert=never
eap_identity=%any
conn CiscoIPSec
keyexchange=ikev1
forceencaps=yes
authby=xauthrsasig
xauth=server
auto=add
EOF
配置 VPN 賬號與密碼
# VPN user accounts and secrets cat > /etc/strongswan/ipsec.secrets <<EOF : RSA ServerKey.der neo : EAP "hWAS5IJWD8NxlQvVFaUVAKid6IFJ6uNO" jam : EAP "1cNEwkfsaN6GzcmWYLedUvJXSpb16UPH" EOF
啟動 strongswan
systemctl enable strongswan systemctl start strongswan
導入客戶端p12證書,直接雙擊Client.p12檔案即可
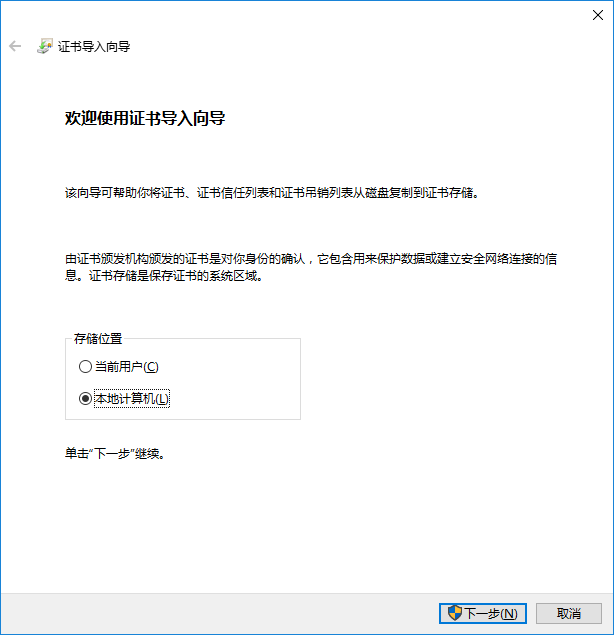 |
選擇“本地計算機”
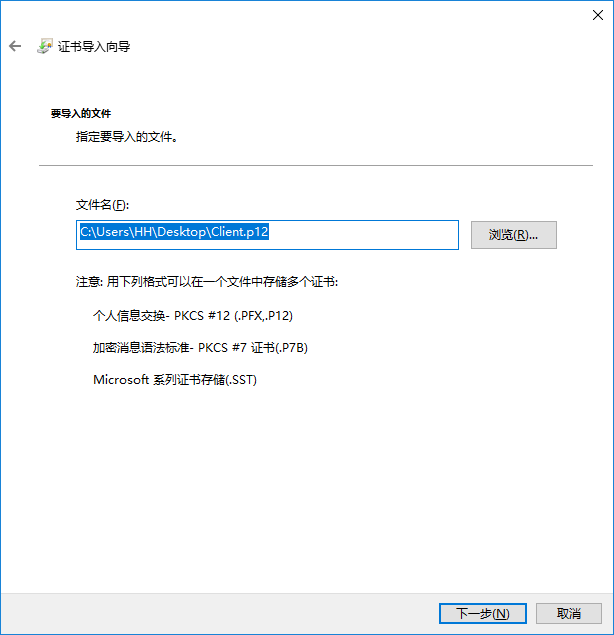 |
下一步
 |
輸入證書密碼,下一步
 |
下一步
 |
點擊“完成”按鈕
 |
證書導入成功
接下來配置 Windows 10 VPN 連結
任務條最右測系統托盤區,點擊網絡表徵圖,再點擊“網絡設置”
 |
點擊“VPN”,然後點擊“添加 VPN 連結”
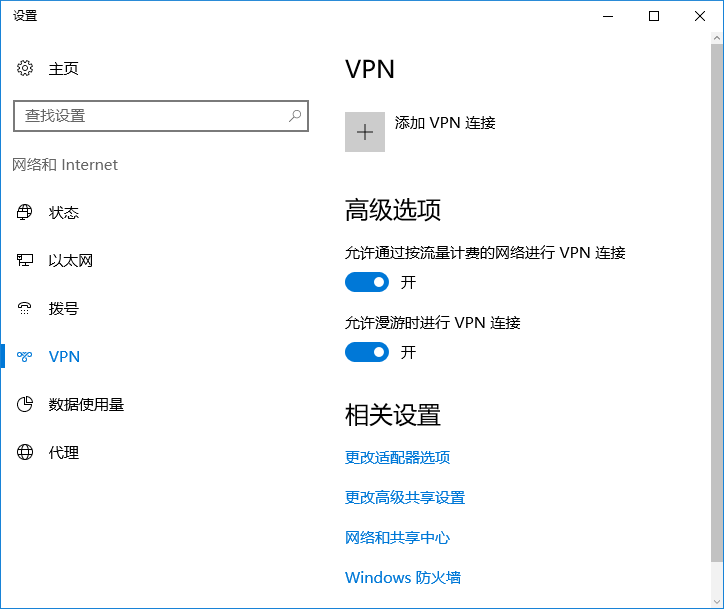 |
填寫信息並保存
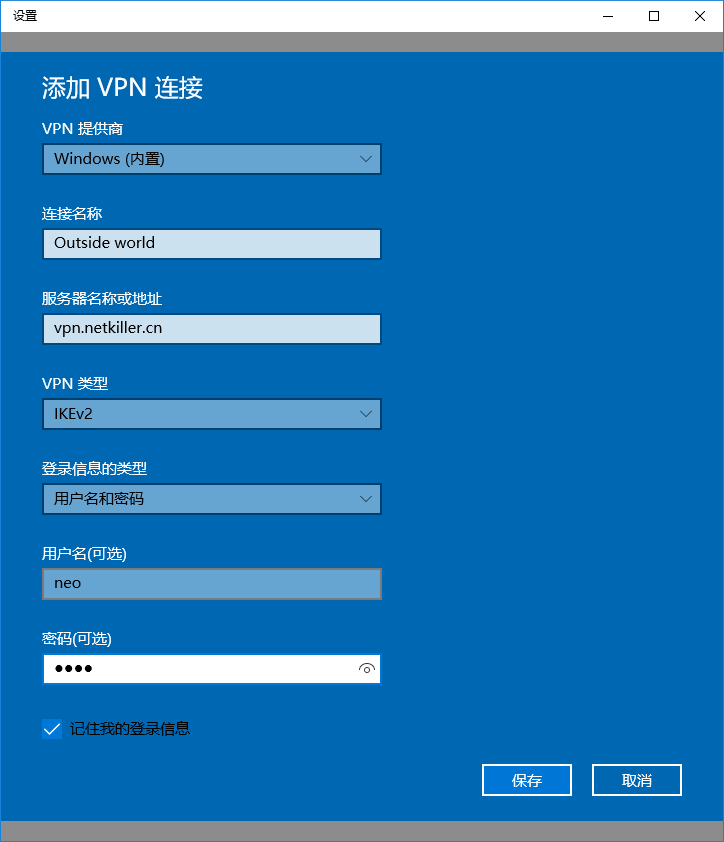 |
點擊“更改適配器選項”
 |
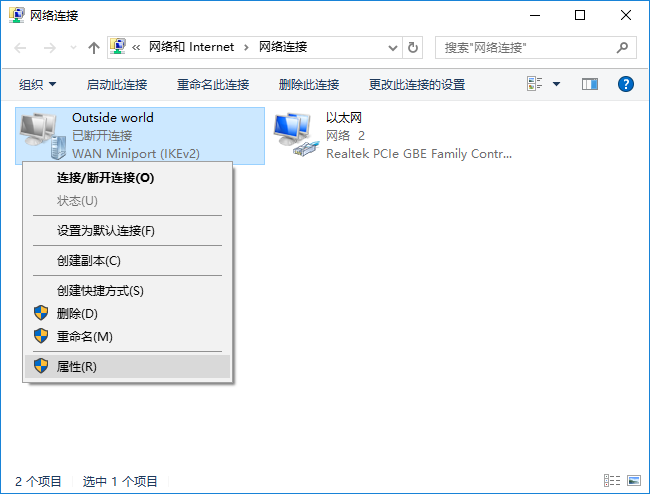
找到VPN網絡適配器,滑鼠右鍵點擊,選擇“屬性”
 |
 |
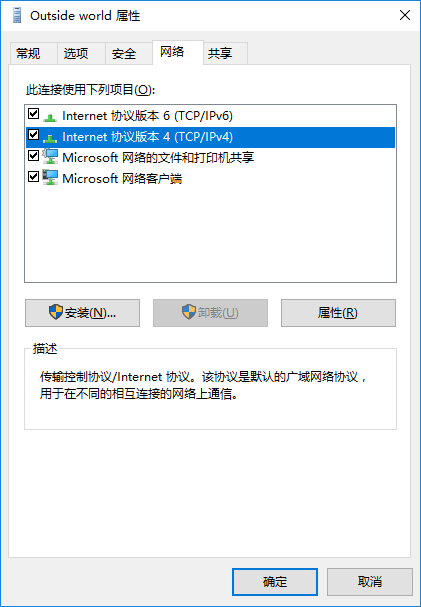
切換到“網絡”選項卡,選中“IPv4”後點擊“屬性按鈕”
 |
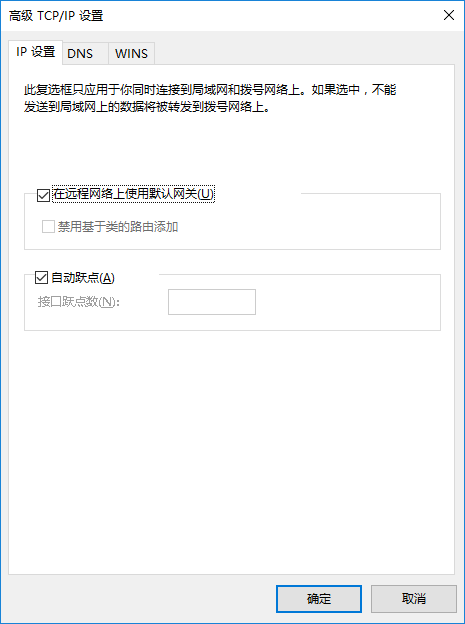
點擊“高級”按鈕
 |
勾選“在遠程網絡上使用預設網關”,然後點擊“確定”按鈕
 |
回到網絡設置界面,點擊VPN表徵圖,再點擊連結
 |
現在查看你的IP地址,正確應該是經過VPN Server 訪問互聯網。